
Hardware-based security
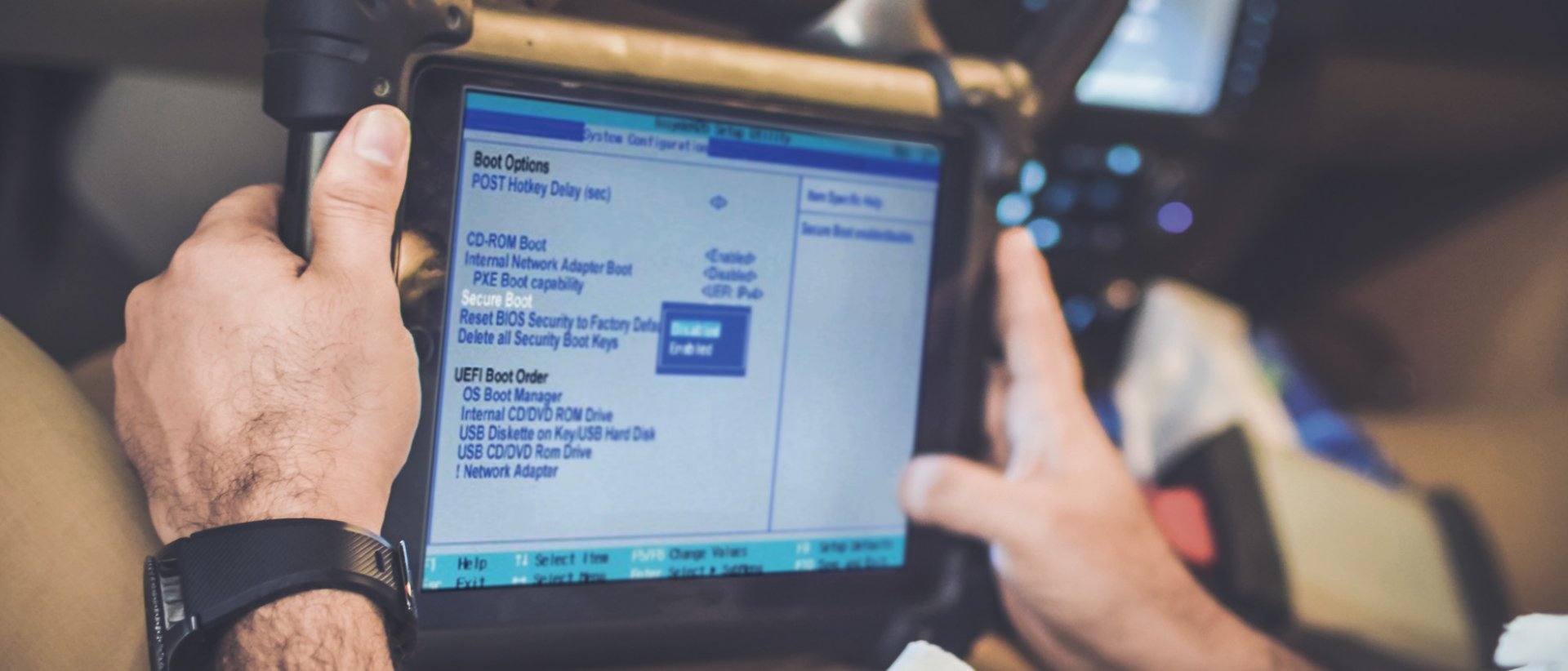
Secure Boot in automotive
Hardware-Based Security as a modern security standard
Times change, and with them the methods. Those who do not cryptographically protect their control units today are close to negligence.
Not only computers, e-mails, apps from the store or social media accounts have long been targets of hackers. Corporate networks and high-level government servers are also victims. Electronic control units (ECU) of networked vehicles are becoming a potential target for hackers. Attackers use bots, for example, to find weak points and compromise software and hardware.
By exploiting security gaps, control units could unintentionally cause speeding or perform counterproductive driving maneuvers. The damage potential is considerable. A particularly dangerous attack would be when malicious code is introduced into an ECU’s boot loader, which then ensures that manipulated device software is loaded when the ECU is started.
Hardware-Based Security as a solution
These weaknesses should be of concern to any product manufacturer who has not previously relied on secure boot procedures.
With this procedure, a so-called public key is implemented in the hardware of all ECUs even before delivery - i.e. part of an asymmetrical encryption procedure. The other part, the private key, remains in a central key management system on a company-owned server or cloud. This private key is now used to digitally sign the firmware of the control unit, also prior to delivery. The code firmware flows into the signature, so that later not only the authenticity of the manufacturer can be checked, but also whether the firmware itself has been maliciously modified.
After delivery and during operation, an attack with a compromised firmware can now be excluded. To do this, the control unit uses its public key to verify the signature of the firmware that was loaded on it. Only if the check is successful is the firmware subsequently loaded by the bootloader. Thanks to the asymmetrical procedure, the signature is considered forgery-proof, because the private key cannot be reconstructed.
"Our strengths lie in mastering the entire chain of cryptography. Starting with key management, the necessary application system, the component hierarchy to coordinate authorizations, right through to the actual implementation in JAVA using JCE (Java Cryptography Extension) or PKCS#11 (Public Key Cryptography Standards)," comments Sebastian Huber, who is responsible for questions relating to hardware-based security at Cognizant Mobility.
In A Nutshell
- Key Management
- Secure Boot
- JCE
- PKCS
- Cloud HSM
- RSA, ECDSA

He and his team are increasingly relying on Cloud Hardware Security Module or HSM. A hardware component that was developed especially for cryptographic operations and, compared to a pure software solution, is better and faster at generating random numbers for the digital key material and signatures. HSM via a cloud additionally guarantees high availability and makes company-owned servers for key management obsolete.
The importance of hardware-based security increases dramatically due to highly automated driving. Manufacturers should only have to put their hand in the fire for verified firmware. It is obvious that with increasingly complex electronic functions and increasingly sophisticated attacks, this is not possible without hardware-based security. So, it's time to rethink quickly.


